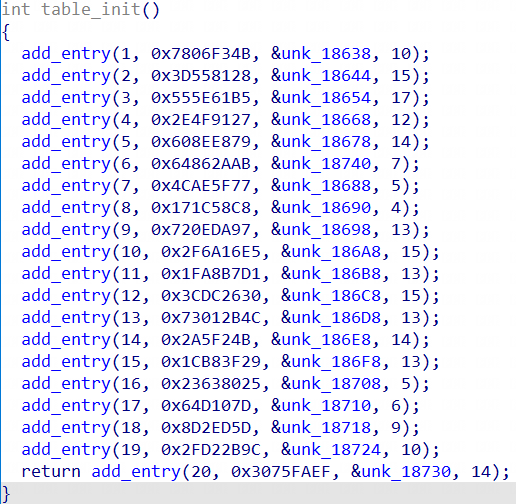
Botnets Never Die: Analysis of the RapperBot Botnet
Overview
RapperBot is an active botnet family first publicly disclosed and named by CNCERT in July 2022. FortiGuard Labs traced its activity back to 2021 in their November 2022 report. In February 2025, RapperBot participated in an attack against Deepseek; its attack behavior has been significantly active since March, with an average of over a hundred targets per day and more than 50,000 bots observed.
This family not only continues to iterate but also leaves provocative messages in its samples. For example, some samples contained an unused string: https://www.youtube.com/watch?v=4fm_ZZn5qaw, which links to a rap song titled "I Am Da Bag." Other samples included strings urging people to follow the rapper 2tallforfood. The authors even asked reverse engineers whether they listened to their music while analyzing the samples and openly taunted our former team, NETLAB360.
It even promised to "leave a new message" in the next update. Unfortunately, we have not received any further communication. The message left in the sample is as follows:
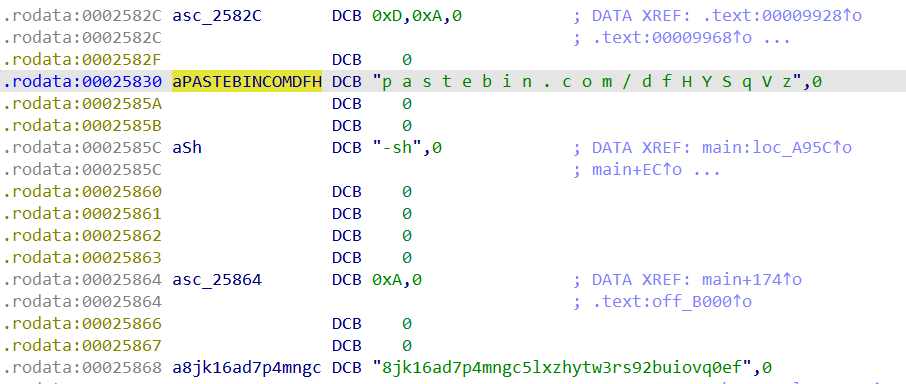
The Pastebin URL in the image, https://pastebin.com/dfHYSqVz, contains the following content after Base64 decoding:
This is rapperbot, rapperbot is in its testing and development stages. Take nothing here seriously.
Brian Krebs approves of this project; he is our number one supporter.
FUCK DOTA3.TAR.GZ (outlaw) AND FUCK xorddos for using those dumb ass low IQ root kits. (they have no idea what's to come)
I love Olivia Rodrigo, soon I will be rich enough to meet her.
Question, Did you guys listen to my music whilst reverse engineering my binary? (https://www.youtube.com/watch?v=4fm_ZZn5qaw)
I can only imagine the Chinese (NETLAB360) researchers not understanding it at all and trying to decode the meaning behind it.
Anyway, 2tall out!
See you guys in the next update, I'll most likely leave another note.
In recent samples, we noticed that RapperBot seems to have started extorting victims, demanding "protection fees" to avoid DDoS attacks.
Donate $5,000 in XMR to (48SFiWgbAaFf75KsRSEEr4iDcxrevFzVmhgfb6Qudss52JK8cCR8bwmUxNBPN2VmqDTucJL3eabiZc5XRYVGkbh6BH58Ytk) to be blacklisted from this and future botnets from us. Contact: horse@riseup.net with TxID and IP Range/ASN.
XLAB has been tracking this family for a long time, and we will share some of our latest findings with the community below.
Bot Scale
When analyzing RapperBot samples, we found that some of the 32 C2 domains it generated had not yet been registered. On April 3, 2024, we proactively registered several of these unused C2 domains. By statistics and analysis of bot hosts (BOTs) accessing our registered domains, we can indirectly obtain information about the RapperBot botnet's scale, distribution, and other details.
In the most recent month of observation, the peak number of BOT IP addresses reached over 50,000, and the BOT activity trend is as follows:
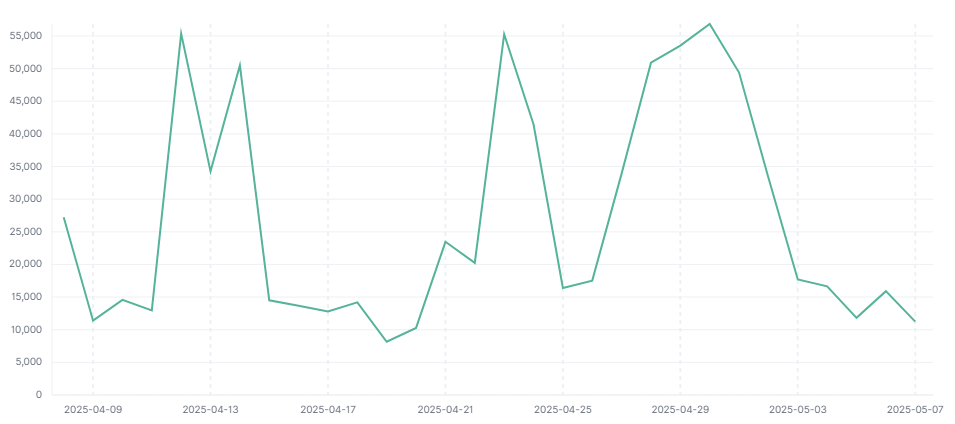
BOT Group Information

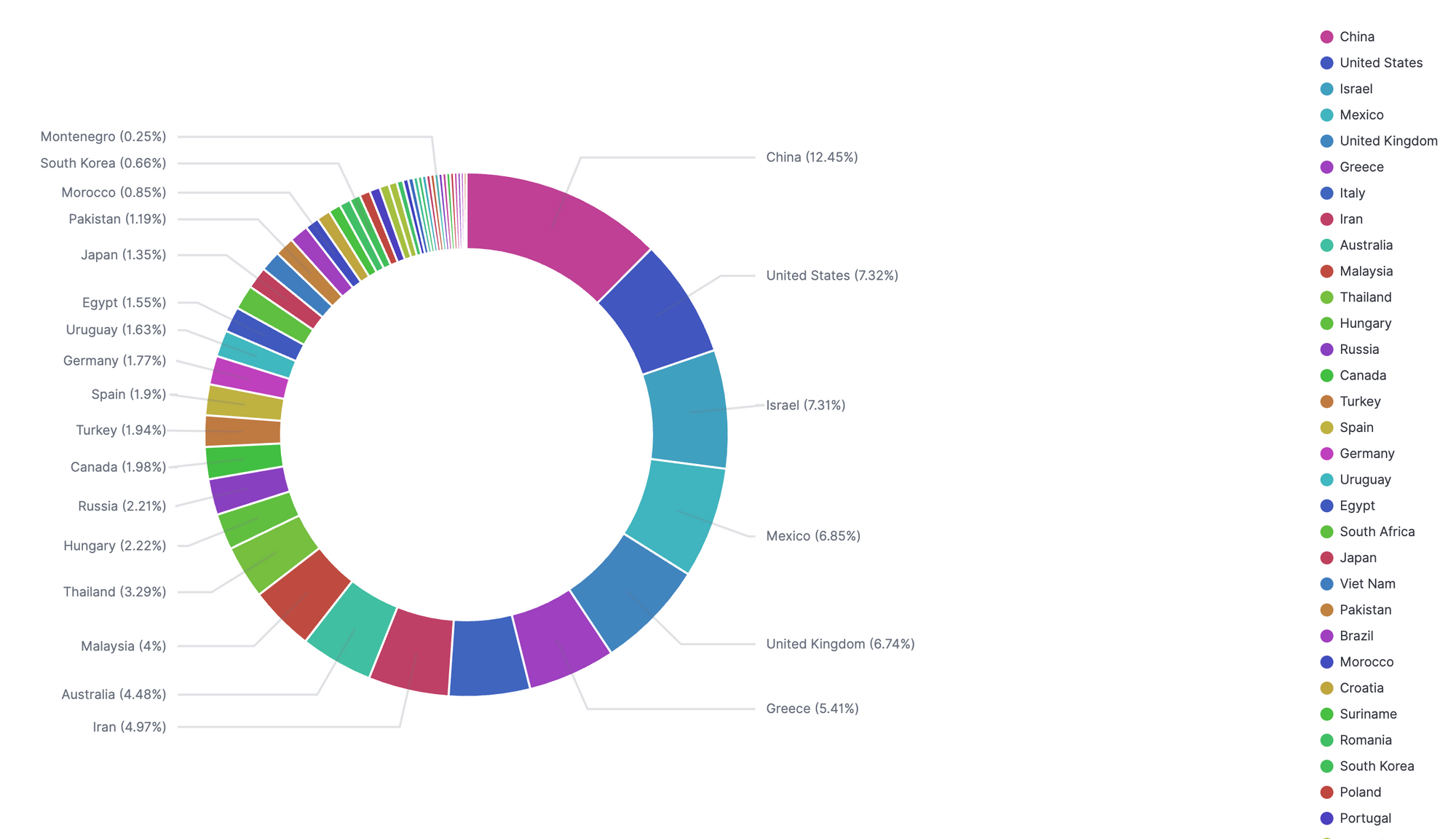
BOT Infected Region Distribution
Infected Devices
According to data analysis from XLAB's HUNTER system, RapperBot malware currently primarily infects IoT devices with public network access capabilities, especially network cameras, and home and enterprise-level routers. These devices usually have default weak passwords or firmware vulnerabilities, making them easy targets for attackers. According to statistics, the top WEB interface titles (Web Titles) of infected devices are as follows:
| WEB Title | Application |
|---|---|
| DVR Components Download | DVR/NVR/Camera |
| Network Surveillance | DVR/NVR/Camera |
| NETSurveillance WEB | DVR/NVR/Camera |
| WEB SERVICE | DVR/NVR/Camera |
| ASUS Login | Router |
| AXIS | DVR/NVR/Camera |
| RouterOS router configuration page | Router |
DDoS Attack Targets
RapperBot's attack targets span various industries, including public administration, social security and social organizations, internet platforms, manufacturing, and financial services. From a geographical distribution perspective, China has the largest number of targets. It has also attacked other important platforms during hot periods, such as: attacking the well-known AI platform DeepSeek during the Spring Festival, and attacking the social media platform Twitter in mid-March.
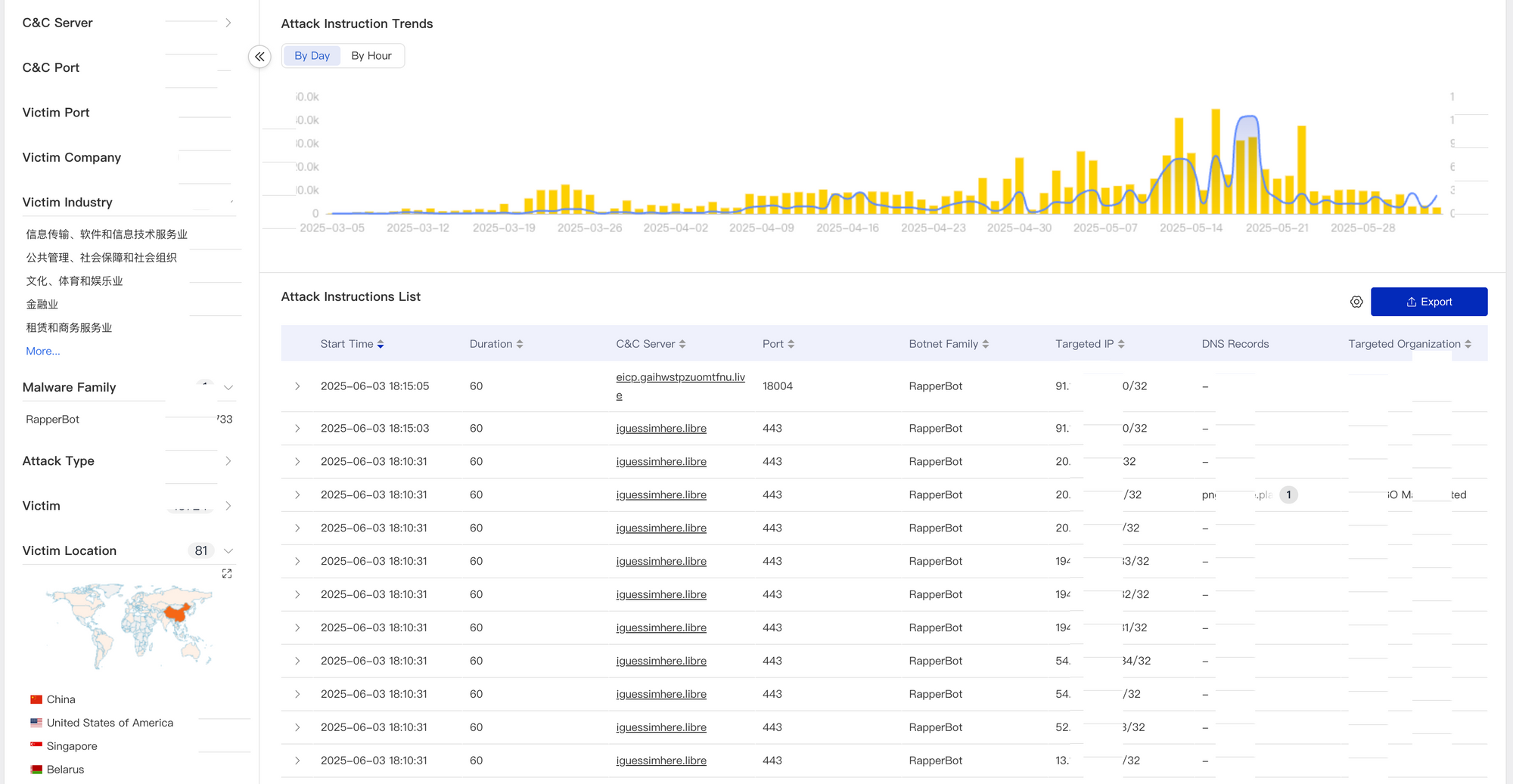
Sample Propagation
Based on our data observations, RapperBot primarily spreads through Telnet weak passwords and by exploiting known vulnerabilities. Currently, the main vulnerabilities it exploits include but are not limited to the following:
| VULNERABILITY | AFFECTED |
|---|---|
| TELNET_Weak_Password | |
| KGUARD DVR TCP_MSGHEAD_CMD | KGUARD DVR |
| CNVD-2021-79445 | Ruijie NBR700 |
| CVE-2021-46229 | D-Link Di-7200G |
| CVE-2023-4473 | Zyxel NAS326 |
| Reolink BaiChuan RCE | Neolink |
| CVE-2020-9054 | ZyXEL NAS |
| Shenzhen TVT | Shenzhen TVT DVR |
| CCTV-DV | Multiple Vendors CCTV-DVR |
| CVE-2020-24581 | D-link DSL-2888A |
| LILIN DVR | LILIN DVR |
Sample Analysis
Through tracking samples of this family, we found that the developer updates the samples every few months and enters an active state. Over more than a year, we have captured 7 variants of this family:
| time | sha1 | ps | decrypt method | login length |
|---|---|---|---|---|
| 2023-07-21 | 8a9a098dabcc09c8a770777f12c71017bb26940b | listening tun0 | mirai string decryption, fixed key (0xDEADBEEF) | 36 |
| 2023-10-15 | d4bca8193b808dcdbdb79367ac688f6f424da36f | listening tun0 | rapperbot custom string decryption | 171 |
| 2023-12-27 | a742f069f604aa302dbfe6ccf0bc481726e76fb6 | listening tun0 | rapperbot custom string decryption | 114 |
| 2024-03-10 | 09dc5f47374410bb05cfd72bc1fa6523a35ec6dc | listening tun0 | mirai string decryption, multiple decryption keys | 60 |
| 2024-06-14 | bc21342317fca22076406873013959ed111cf8dc | Firmware update in progress | mirai string decryption, multiple decryption keys | 90 |
| 2024-10-10 | cc687e707919c4176ab03bdc76ab01bbaa7c0e22 | Firmware update in progress | mirai string decryption, multiple decryption keys | 120 |
| 2025-03-30 | 4a0aa2b7f357164dbd49c0c6ab71a3c73e148aaa | Firmware update in progress | rapperbot custom string decryption | 120 |
Samples of different variants within this family are largely similar, with modifications mainly focused on message data structures, DNS-TXT record parsing methods, and string decoding. Functionally, they are primarily used for DDoS attacks, with proxy capabilities added starting from October 2024.
C2 Acquisition
Unlike most botnets, RapperBot resolves its C2 domain through DNS-TXT records. So far, we have identified four different TXT record formats:
| time period | TXT record format |
|---|---|
| 2023.07 - 2024.04 | IP,IP,IP |
| 2024.06 - 2024.10 | <IP><IP><IP> |
| 2024.10 - 2025.03 | IP |
| 2025.03 - now | EncryptedString |
Regarding C2 ports, early versions used fixed ports such as 1111, 1024, and 9999. In the latest samples, however, a random port is selected from a pool of 35 possible options:
443, 4443, 993, 995, 25565, 1935, 3478, 27015, 7777, 3724, 5222, 7000, 5223, 4444, 3074, 27014, 27050, 3544, 6666, 2222, 22022, 2022, 19153, 3389, 37777, 6036, 34567, 5000, 10554, 554, 18004, 9000, 35000, 10001, 9001
Encryption and Decryption Algorithms
String Decryption Algorithm
RapperBot has used three encryption algorithms. Early versions used the same algorithm as Mirai, followed by the development of unique custom decryption algorithms and an enhanced version of the Mirai decryption algorithm, which are rotated across multiple variants:
- Improved Mirai source code string decryption method, adding different 4-byte decryption keys for each string and continuing to use Mirai's decryption function.
- Custom decryption method, using a variable-length key that is encrypted twice before being applied. The data is then decrypted using multi-byte XOR with the processed key.
C2/DNS-TXT Decryption Algorithm
Starting from March 2025, RapperBot uses a custom decryption algorithm to decrypt TXT records and C2 domains:
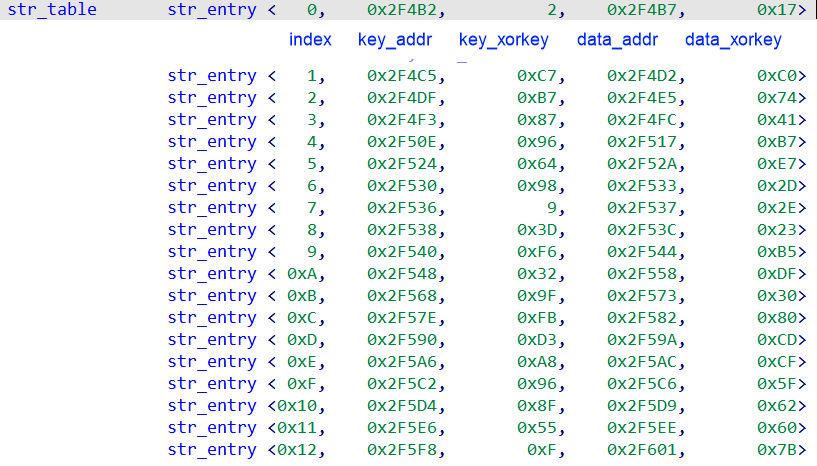
By decrypting the string table, we can obtain 3 strings:
| str | desc |
|---|---|
| ipWPeY43MhfFBt8ZCSN2KTdD6nEkmGjwx7vJR5rogzbcqHsXUQuyVA9L | Table used for decryption algorithm |
| WF6i6VEcfjnyqtGKxism65YwRE9VYzzzbtLgLD4tWEsnZLgbJfuE94qtvTqGgVG3ScFtsfcxqTNtYKRWQTqNBqp6VLMv2p | Encrypted second-level domain list |
| WMKFVCnSHDrC89fvKgCShwmRjEx8 | Encrypted third-level domain list |
The top-level domain string is not written to the string table but is written to a global variable via the stack:

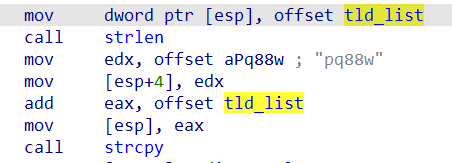
After decryption with the unique algorithm, the parts of the C2 domain can be obtained. The decryption algorithm and results are as follows:
def decodeTXT(data:str):
key = "ipWPeY43MhfFBt8ZCSN2KTdD6nEkmGjwx7vJR5rogzbcqHsXUQuyVA9L"
a = key.find(data[0])
b = key.find(data[1])
seed = 56*a+b
magic = 1000000000 + 0x62B846D
S = bytearray(range(56))
T = bytearray(56)
tseed = seed
for i in range(55, 0, -1):
tseed = (magic * tseed + 0x3039)&0xffffffff
index = tseed%(i+1)
S[i], S[index] = S[index], S[i]
for i in range(56):
T[S[i]] = i
res = bytearray()
for i in data[2:]:
index = (T[key.find(i)] - (len(data)-2) - seed)%56
res.append(index)
length = ceil(len(res) * log2(56) / 8)
res3 = bytearray(length)
for t1 in res:
carry = t1
for i in reversed(range(len(res3))):
temp = res3[i] * 56 + carry
res3[i] = temp & 0xFF
carry = temp >> 8
while len(res3) > 0 and res3[0] == 0:
del res3[0]
return res3 if len(res3) > 0 else bytearray(b'\x00')
Third-level domains: KDXA|EICp|kHbW|YFrV
Second-level domains: ByxWGIMPbwiSkniw|gwYhHCOrybwjWuzh|GaihWstPZUoMtfnU|zkUAFIMFDwVETXJQ
Top-level domains: info|live
Using "|" to split each part of the domain will eventually generate 32 C2 domains, and one will be randomly selected for DNS-TXT resolution. The TXT record string is decrypted using the same decryption algorithm:
TXT record: i7do6u4FtLeeMjmnwWczxKJmtoRRvgCCqiinWW9EUtVpLx38db5xrCfr8mHmsxmutZ4C8fXL2jhGVzfdUQmvvnzZW7pCJmUpi
Decrypted: 5.230.39.10|5.230.68.153|82.24.200.59|82.24.200.68|62.146.235.220|5.230.227.190|5.230.227.191|5.230.227.237|5.230.227.238
Network Protocol
RapperBot’s network protocol is relatively simple, with no key exchange or complex encryption involved; The payload is only XORed with a single byte (using a variable key); Across multiple variants, only the check-in information and message encoding have been modified.
Register
RapperBot's login packet format differs across versions, sometimes adding fields, sometimes reducing them, but always including hostname, source, stunIP, and localIP, and filling unused space with non-zero random numbers. The latest version adds network information fields, with a total size of 120. Below is a description of the relevant structure:
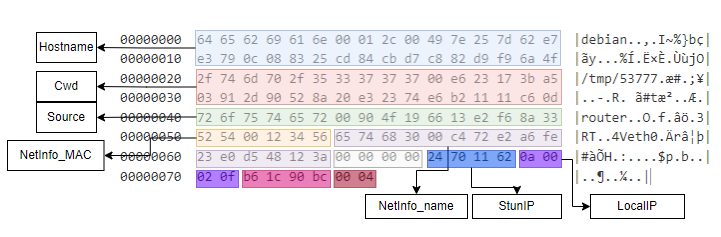
Message Encoding
In terms of network communication, different versions of message formats have slight differences, but they usually consist of 3 parts: Header, Payload, and RandData. Taking the latest sample as an example, the Header adds a checksum field, and RandData is randomly generated from the string table q1x4fyntb3i0umw2gzcr9a5jkv7o8pl6eohds:
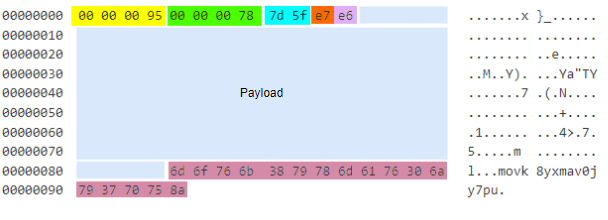
Message structure:
struct rapperbot_packet{
int32 total_size;
int32 payload_size;
int16 checkcode;
int8 xorkey;
int8 packet_type;
int8 payload[payload_size];
int8 randdata[total_size-payload_size];
};
Known message types and their functions:
| PacketType | Desc |
|---|---|
| 1 | Login |
| 2 | Confirm |
| 3 | Pong |
| 4 | HeartBeat |
| 5 | Start Attack |
| 6 | Stop Attack |
| 9 | Proxy Enable |
| 10 | Proxy Disable |
| 11 | Proxy Create |
| 12 | Proxy Start |
| 13 | Proxy Close |
Contact Us
Readers are always welcomed to reach us on twitter.
IOC
XMR wallet address:
48SFiWgbAaFf75KsRSEEr4iDcxrevFzVmhgfb6Qudss52JK8cCR8bwmUxNBPN2VmqDTucJL3eabiZc5XRYVGkbh6BH58Ytk
C2 Domain:
iranistrash.libre
churchofhollywood.libre
iguessimhere.libre
KDXA.ByxWGIMPbwiSkniw.info
KDXA.ByxWGIMPbwiSkniw.live
KDXA.gwYhHCOrybwjWuzh.info
KDXA.gwYhHCOrybwjWuzh.live
KDXA.GaihWstPZUoMtfnU.info
KDXA.GaihWstPZUoMtfnU.live
KDXA.zkUAFIMFDwVETXJQ.info
KDXA.zkUAFIMFDwVETXJQ.live
EICp.ByxWGIMPbwiSkniw.info
EICp.ByxWGIMPbwiSkniw.live
EICp.gwYhHCOrybwjWuzh.info
EICp.gwYhHCOrybwjWuzh.live
EICp.GaihWstPZUoMtfnU.info
EICp.GaihWstPZUoMtfnU.live
EICp.zkUAFIMFDwVETXJQ.info
EICp.zkUAFIMFDwVETXJQ.live
kHbW.ByxWGIMPbwiSkniw.info
kHbW.ByxWGIMPbwiSkniw.live
kHbW.gwYhHCOrybwjWuzh.info
kHbW.gwYhHCOrybwjWuzh.live
kHbW.GaihWstPZUoMtfnU.info
kHbW.GaihWstPZUoMtfnU.live
kHbW.zkUAFIMFDwVETXJQ.info
kHbW.zkUAFIMFDwVETXJQ.live
YFrV.ByxWGIMPbwiSkniw.info
YFrV.ByxWGIMPbwiSkniw.live
YFrV.gwYhHCOrybwjWuzh.info
YFrV.gwYhHCOrybwjWuzh.live
YFrV.GaihWstPZUoMtfnU.info
YFrV.GaihWstPZUoMtfnU.live
YFrV.zkUAFIMFDwVETXJQ.info
YFrV.zkUAFIMFDwVETXJQ.live
Download Domain:
pool.rentcheapcars.sbs
o0s.cc
4v.wtf
zyb.ac
Hardcode backup C2:
86.104.72.130 Canada|Ontario|Toronto AS208913|Mouk, LLC
194.156.98.15 China|Hongkong|Hongkong AS44477|STARK INDUSTRIES SOLUTIONS LTD
94.131.118.154 France|Ile-de-France|Paris AS44477|STARK INDUSTRIES SOLUTIONS LTD
5.231.3.32 Germany|Hessen|Frankfurt am Main AS12586|GHOSTnet GmbH
5.231.4.35 Germany|Hessen|Frankfurt am Main AS12586|GHOSTnet GmbH
185.248.144.209 Italy|Lazio|Rome AS44477|STARK INDUSTRIES SOLUTIONS LTD
45.150.65.202 United States|New Jersey|Secaucus AS44477|STARK INDUSTRIES SOLUTIONS LTD