New Zero-Detection Variant of Melofee Backdoor from Winnti Strikes RHEL 7.9
Background
On July 27, 2024, XLab's Cyber Threat Insight and Analysis System(CTIA) detected an ELF file named pskt from IP address 45.92.156.166. Currently undetected on VirusTotal, the file triggered two alerts: an Overlay section and a communication domain mimicking Microsoft. Our analysis identified it as a Melofee backdoor variant, specifically targeting Red Hat Enterprise Linux (RHEL) 7.9.
Melofee, a C++ backdoor, enables data collection, process management, file handling, and shell access. Originally exposed by ExaTrack in March 2023 and attributed to the APT group Winnti, this latest variant has notable upgrades. Structurally, it embeds an RC4-encrypted kernel driver to mask traces of files, processes, and network connections. Functionally, it adds improvements in persistence, single-instance control, and function ID design.
By examining the sample's Run-Time Type Information (RTTI), we observed source-level modifications. For instance, the network connection class name has changed from TLSSocket in earlier samples to TlsConn in this variant, suggesting ongoing reconstruction and use of Melofee beyond the security community's radar.
Notably, during our investigation, we encountered an intriguing misattribution. The new variant utilizes the C2 address filemanage.micrsofts-file.com. According to Passive DNS (PDNS) records, this C2's second-level domain, micrsofts-file.com and its associated domain, www.micrsofts-file.com resolved to IP address 91.195.240.123 between November 2023 and June 2024. This IP also appeared in BlackBerry's July 2024 report on the APT group SideWinder and has been flagged as malicious by several security vendors on VirusTotal. Does this imply that Melofee has circulated among multiple organizations, becoming a cross-group tool rather than being exclusive to a single group?
We believe this is unlikely. The IP address 91.195.240.123 is a parking IP provided by domain registrar NameSilo. Labeling it as malicious likely constitutes a false positive. NameSilo automatically resolves new registered second-level domains and "www" subdomains to this IP, leading to potential misattributions, as legitimate domains, unrelated malicious domains, and APT activities may all share this IP.
Due to limited visibility, we currently lack details on the attacker’s entry methods and goals. We invite others to share insights to enrich the technical landscape. Given the low detection rate of this sample and Melofee’s stealth, we’re sharing these findings with the community for broader cybersecurity awareness.
This report covers:
- Overlay structure and decryption method
- Driver module’s functionalities
- Melofee’s capabilities
Technical Details
We have captured a single sample with the following details:
MD5: 603e38a59efcf6790f2b4593edb9faf5
Magic: ELF 64-bit LSB executable, x86-64, version 1 (SYSV), statically linked, BuildID[sha1]=48bcb3f7c78bc746e25264058a76145b63bbf440, for GNU/Linux 3.2.0, stripped
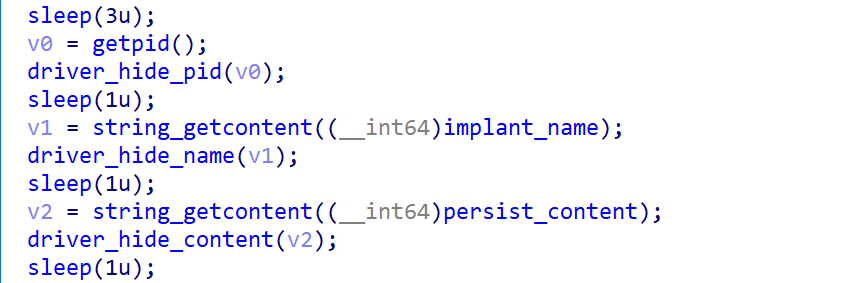
This variant operates in two modes based on launch parameters: Infection Mode and Management Mode.
-
Infection Mode (No Parameters)
When launched without parameters, Melofee enters Infection Mode, performing the following:- Enforces single instance via
/tmp/lock_tmp1 - Achieves persistence via
crontab, disguising the process name as[md]orwwwwww - Decrypts and installs a driver module for stealth across files, processes, network connections, and directories
- Decrypts and connects to its C2 server, awaiting commands
- Enforces single instance via
-
Management Mode (With Parameters)
When launched with parameters, Melofee enters Management Mode, controlling driver hiding functionality:- hide: Activates hiding features
- show: Deactivates hiding
- kill: Terminates the process
This design enables flexible operation across infection and management needs. The next sections will cover Melofee’s decryption, driver module, and backdoor functions in detail.
Part 1: Decryption
Melofee stores its RC4-encrypted driver module as an overlay appended to the file’s end, using a structure called drv_overlay:
struct drv_overlay {
int encrypted_payload[payload_size];
int payload_size;
char flag[12];
}
In this sample, the flag is set to "EV#?YLFAkoip" and payload_size is 0x6a08. The encrypted_payload spans 0x6a08 bytes backward from payload_size.
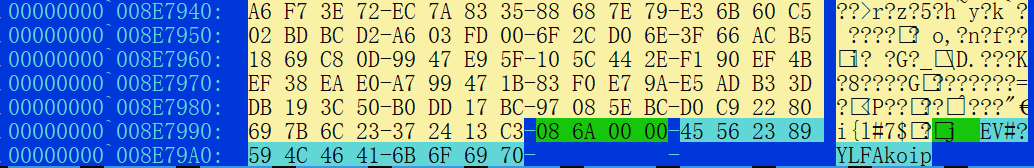
Using the key 87JoENDi, the encrypted_payload is decrypted to reveal the driver module kworkerx, designed for RHEL 7.9 with kernel version 3.10.0.
The C2 configuration is also RC4-encrypted, using the same key 87JoENDi.
Encrypted C2 Data:
00000000 a2 a4 96 0e 27 ee 40 54 a5 3a 52 8e 65 cf b1 e1 |¢¤..'î@T¥:R.eϱá|
00000010 29 69 32 86 ae 56 4d 28 a2 b8 da 6e e1 05 5d 65 |)i2.®VM(¢¸Úná.]e|
00000020 fc 86 88 50 43 17 |ü..PC.|
Decrypted C2 Configuration:
0:filemanage.micrsofts-file.com:443:60
This configuration includes the following elements:
- Connection Type
- C2 Domain
- C2 Port
- Interval
Part 2: Driver Module Analysis
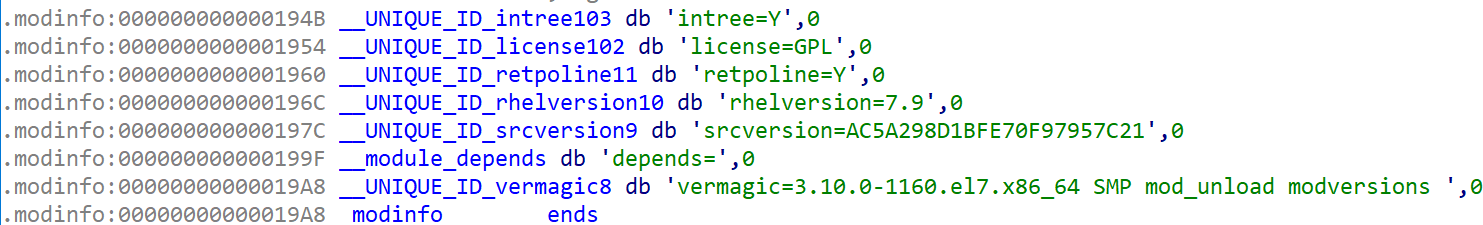
The decrypted driver module, kworkerx, has the following basic information:
MD5: 839f60efee25f07df7b23ba9d6bef892
Magic: ELF 64-bit LSB relocatable, x86-64, version 1 (SYSV), BuildID[sha1]=c440028449ebce5c899a51ef0eb4d7fc43493253, not stripped
Through analysis, we confirmed that kworkerx is a modified version of the open-source project Reptile. The original Reptile project supports 12 functions, categorized into two main types: hiding and backdoor capabilities. kworkerx primarily utilizes the hiding functions.
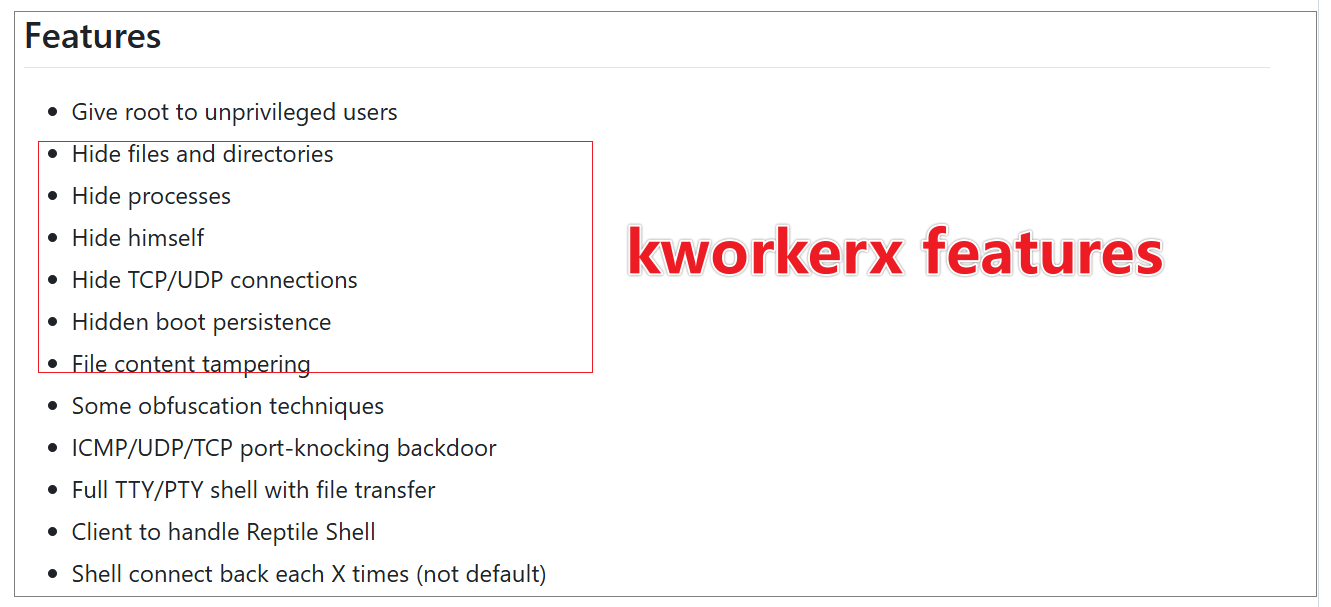
Hiding Mechanisms in kworkerx
- Network Communication Hiding:
kworkerxhooks thetcp4_seq_showfunction within its initialization routine, effectively hiding all network traffic on port 443. - File, Process, and Directory Hiding: To conceal files, processes, and directories,
kworkerxhooks several functions, includingfillonedir,filldir,filldir64, andvfs_read.
Communication with User Space
kworkerx also hooks the inet_ioctl function to facilitate communication with user-space applications and receive control commands.
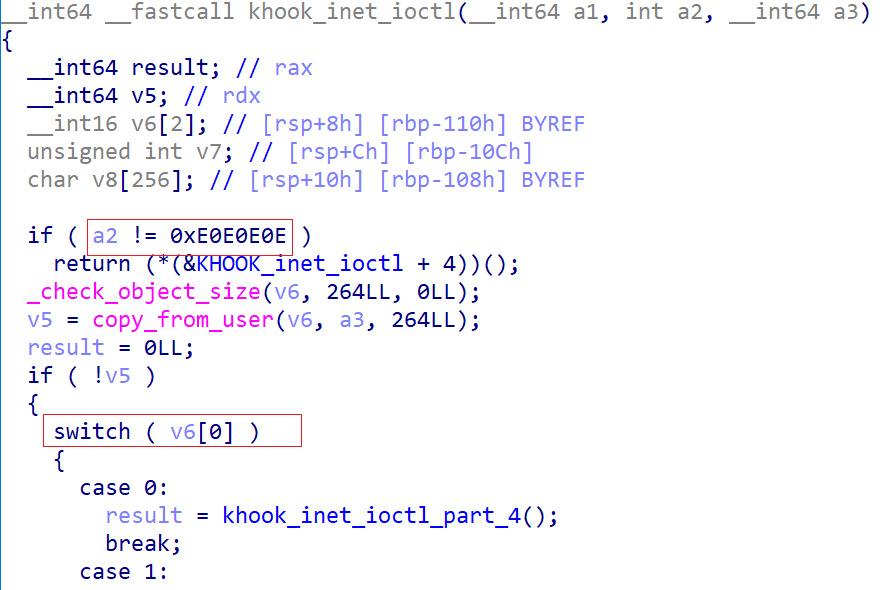
When a user-space application calls the ioctl function with the second parameter set to 0xE0E0E0E, it triggers the handler function khook_inet_ioctl in kworkerx. Within this function, kworkerx interprets the third parameter to either enable or disable specific hiding functions, providing fine-grained control over its concealment capabilities.
| Arg.cmd | Capability |
|---|---|
| 0 | show all |
| 1 | hide all |
| 2 | hide proc |
| 3 | show proc |
| 5 | file tampering |
| 7 | hide file,dir |
| 8 | unhide_chdir |
| 9 | hide_chdir |
Part 3: Melofee Analysis
After installing the kworkerx kernel driver module via the init_module function, Melofee enables TCP connection hiding by default. Additional hiding features, such as process, directory, and persistence concealment, are activated through control commands sent via IOCTL.
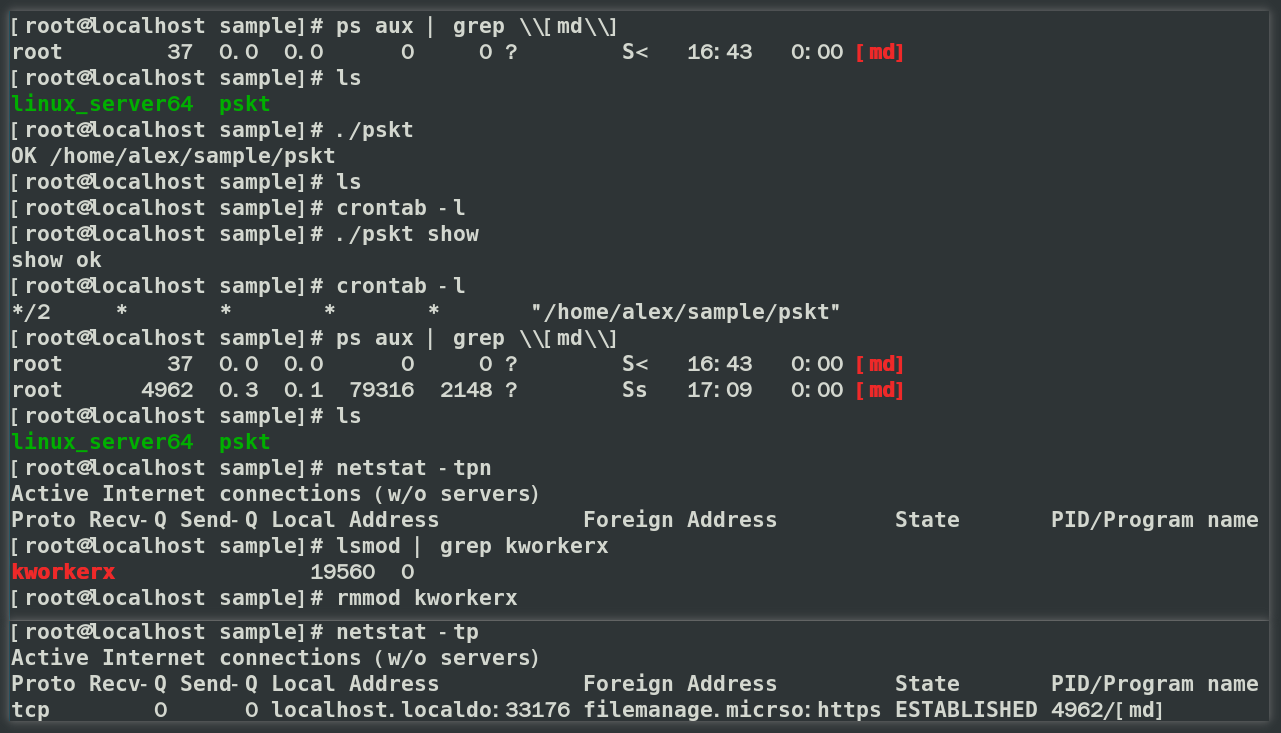
When executed without parameters in a virtual machine, Melofee successfully concealed its process, the sample file, the persistence script, and network connections. Running the sample again with the show parameter revealed the process, sample file, and persistence script, while the network connection remained hidden. Finally, using the rmmod command to unload the kworkerx module restored visibility to the previously hidden network connection.
After installing the driver module, Melofee decrypts the C2 configuration and establishes communication, waiting to receive and execute commands. The functionality of this sample aligns with the description provided in the ExaTrack analysis report, though there are differences in function IDs.
| CMD ID | Capability |
|---|---|
| 0x11 | uninstall |
| 0x22 | collect device info |
| 0x33 | launch new command thread |
| 0x34 | write file |
| 0x35 | read file |
| 0x36 | create new socket |
| 0x37 | list directory |
| 0x38 | create directory |
| 0x3a | delete directory |
| 0x3b | create process to exec cmd |
| 0x3c | exec command with output (including set new c2 ip) |
| 0x3d | collect process info |
| 0x3e | kill process |
| 0x3f | launch shell |
| 0x7b | ping back |
Summary
Melofee offers straightforward functionality with highly effective stealth capabilities. Samples of this malware family are rare, suggesting that attackers may limit its use to high-value targets. Network administrators can check for infection by looking for artifacts like the /tmp/lock_tmp1 file and the kworkerx module. If signs of infection are detected, follow the previous steps to remove associated drivers, processes, files, and persistence mechanisms.
We welcome readers to share additional insights and intelligence. If you’re interested in our research, feel free to reach out to us via Platform X.
IOC
MD5
603e38a59efcf6790f2b4593edb9faf5 *pskt
839f60efee25f07df7b23ba9d6bef892 *kworkerx
C2
filemanage.micrsofts-file[.]com:443
Downloader
http://45.92.156[.]166/klove/pskt
